Making Your IoT Devices Securely Accessible: An SSH Remote IoT Device Example
Connecting to your IoT devices from afar can feel a bit like magic, but it needs to be safe magic. You want to reach your smart gadgets, maybe a little sensor on the other side of the house or a micro-controller at a remote site, and you want to do it without leaving a digital door wide open for just anyone. This is where a secure shell, or SSH, steps in, offering a reliable way to manage your tiny computers. It's really about having a strong, private conversation with your devices, ensuring everything you send or receive stays just between you and them.
Think about all those small, internet-connected things around us today. From home automation hubs to industrial sensors, these devices are becoming more and more common, which means keeping them secure is more important than ever. If you're working with these kinds of devices, you've probably thought about how to talk to them when you're not right next to them. This is where a good, solid method for remote access, like SSH, becomes incredibly helpful, you know?
This article will walk you through how SSH makes remote access to your IoT devices not just possible, but also very secure. We'll look at some real-world examples, talk about setting things up, and even touch on how to handle those little bumps in the road that sometimes pop up. So, if you're keen to get a better handle on keeping your remote IoT gadgets safe and sound, you're in the right place.
Table of Contents
- Why SSH Matters for Your IoT Gadgets
- Setting Up SSH on Your IoT Device
- Everyday SSH Examples with IoT Devices
- Troubleshooting Common SSH Hurdles
- The Future of IoT Security with SSH
- Frequently Asked Questions
Why SSH Matters for Your IoT Gadgets
When you're dealing with small devices, especially those out in the wild or in places you can't easily reach, getting to them and making changes can be a challenge. That's why SSH, or Secure Shell, is such a big deal for IoT. It's a way to log in to another computer over a network, but it does so in a way that's very, very secure. It basically creates a private tunnel for your commands and data, keeping prying eyes out. This is a bit like having a secret handshake that only you and your device know, so, you know, only authorized people get in.
The Secure Shell Protocol: A Quick Look
The SSH protocol, sometimes just called Secure Shell, is a method for securely logging in from one computer to another. It's not just for logging in, though; it also helps with transferring files safely. It was first developed by Tatu Ylönen as a free version and has since been further improved by OpenBSD, which is pretty cool. It provides a few different ways for really strong authentication, meaning it's quite good at making sure the person trying to connect is actually who they say they are. This is used in nearly every data center and in every large business, so it's a very trusted tool, actually.
Keeping Your IoT Safe
Security for IoT devices is a big concern today. With so many devices connected, each one could be a potential weak spot. SSH helps a lot here. It scrambles all the data that goes between your computer and the IoT device, making it unreadable to anyone trying to snoop. Plus, it uses host keys, so your client computer remembers the key for a particular device. This helps confirm you're connecting to the right device and not some imposter, which is a very important safety measure. It's about protecting your data and your devices from unauthorized access, naturally.
Setting Up SSH on Your IoT Device
Getting SSH ready on your IoT device is a pretty straightforward process, but it involves a few key steps to make sure everything is secure and works as it should. The main idea is to use something called an SSH key pair instead of just a password. A key pair has two parts: a private key that stays on your computer and a public key that goes on the IoT device. This method is much more secure than relying solely on passwords, which can sometimes be guessed or stolen, you know?
Generating SSH Keys
To begin, you'll need to create your SSH key pair. Most Linux and macOS systems have a tool built-in for this. You might type a command like `ssh-keygen` in your terminal. This command will create two files, typically `id_rsa` (your private key) and `id_rsa.pub` (your public key), usually stored in a hidden `.ssh` folder in your home directory. For instance, you can copy your public key to your clipboard by entering `pbcopy < ~/.ssh/id_rsa.pub` in your terminal. This is a really handy way to get it ready for the next step, as a matter of fact.
Sometimes, you might need a special key pair for a specific connection, like connecting to an SSH proxy server. In such cases, you wouldn't use your default `id_rsa` key. You'd generate a new one and tell your SSH client to use that particular key. This helps keep your main key safe and separate from other connections, which is a smart security practice. If you're on Windows, tools like PuTTY can help you generate these keys and manage your SSH connections, too it's almost a must-have for Windows users.
Adding Your Key to the IoT Device
Once you have your public key, the next step is to get it onto your IoT device. You'll usually add this public key to a file called `authorized_keys` in the `.ssh` directory of the user account on your IoT device. This tells the device, "Hey, if someone tries to connect with the private key that matches this public key, let them in without a password!" For example, after setting up Git on a new work computer and generating my SSH key, I added it to GitLab. This is the same principle for IoT devices. This makes logging in much smoother and safer, basically.
For persisting your identity, especially on a Mac, you can add your identity using the keychain, as some experts point out. This means you won't have to enter your passphrase every time you connect, which is very convenient. It's a small step that makes a big difference in your daily workflow, like your computer just remembers your secret handshake for you.
Everyday SSH Examples with IoT Devices
Now that your SSH is all set up, let's look at what you can actually do with it. SSH isn't just for logging in; it's a versatile tool that helps you manage your remote IoT devices in many practical ways. From running commands to moving files, it's like having a direct line to your tiny computer, no matter where it is, you know?
Connecting and Running Commands
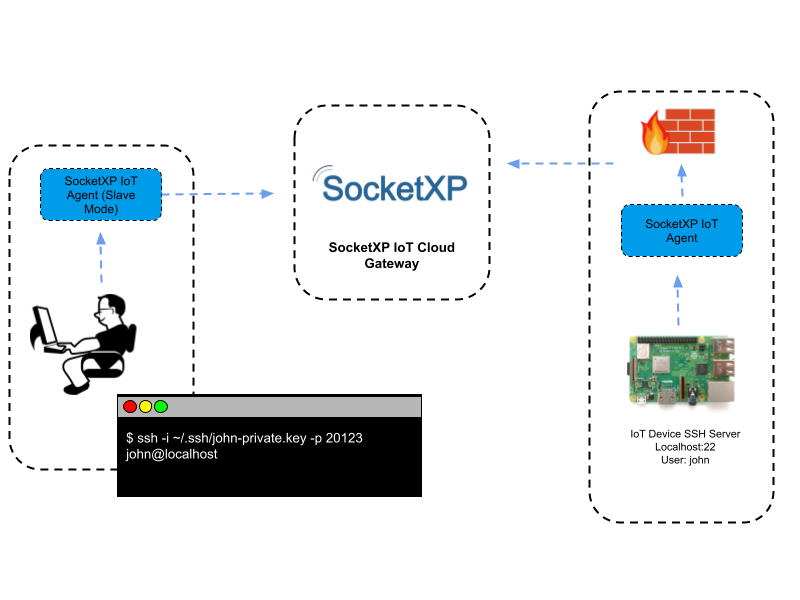
The most common use of SSH is to simply connect to your remote IoT device and run commands as if you were sitting right in front of it. You'd typically use a command like `ssh username@ip_address` in your terminal. Once connected, you can do anything you'd normally do on the device's command line: check its status, start or stop services, install updates, or even restart it. It's a bit like having a remote control for your device's brain, so you can issue instructions from anywhere.
Moving Files Around
Another incredibly useful feature of SSH is its ability to securely transfer files. This is often done using a command called `scp` (secure copy protocol), which is built on SSH. For instance, if you need to copy an entire directory from your local machine to your remote IoT device, `scp` is your friend. I've personally looked up how to copy directories from a local machine to a remote one, and it's quite simple once you get the hang of it. You can send configuration files, software updates, or even collected data back to your main computer, which is really handy.
Dealing with X11 Forwarding
Sometimes, your IoT device might be running a graphical application that you want to see or interact with from your local machine. This is where X11 forwarding comes in. If you run `ssh` and your display isn't set, it means X11 forwarding isn't happening. To check if SSH is forwarding X11, you'd look for a line that says "requesting X11 forwarding" in the SSH output. This feature lets you run graphical programs on your remote IoT device and see their windows appear on your local desktop, almost like magic, you know?
Troubleshooting Common SSH Hurdles
Even with a robust tool like SSH, you might run into a few bumps along the way. It's pretty normal, actually. Knowing some common issues and how to tackle them can save you a lot of time and frustration when you're working with your remote IoT devices. These aren't huge problems, just little things that need a bit of attention, in a way.
Key Pair Woes
One common issue I've seen is related to SSH key pairs. For example, I met this issue after I changed my Apple ID password, so I updated my Apple ID and restarted my Mac. Suddenly, Git pull commands were failing because the SSH connection was messed up. This often happens when your system's SSH agent or keychain gets confused about which key to use or where it's stored. Making sure your SSH agent has the correct key loaded and is set to persist can fix this. It's a bit like your computer forgetting where it put its car keys, but once you help it find them, everything starts working again, you know?
Another scenario is when you're trying to clone a project after installing Git and adding your SSH key, but you get an error. This can be because the system isn't picking up the right key or there's a permission issue with your key files. Double-checking file permissions (`chmod 400 ~/.ssh/your_key`) and ensuring your public key is correctly added to the remote service (like GitHub or GitLab) usually sorts it out, which is a good thing to remember.
Connection Refused or Script Errors
Sometimes, you might try to connect to your IoT device and get a "connection refused" message. This could mean SSH isn't running on the device, a firewall is blocking the connection, or you're trying to connect to the wrong port. It's worth checking the SSH service status on your IoT device first. Or, perhaps, you might encounter an error where your remote script returns 255, and SSH just gives you that result. This means the script you tried to run on the remote device had an issue. Showing the script itself can often help figure out what went wrong. It's like asking a friend to do something, and they just say "no" without explaining why, so you need more information to help them out, you know?
The Future of IoT Security with SSH
The secure shell protocol is widely used, and it's constantly being improved to stay ahead of new threats. Keeping your SSH connections secure is an ongoing task, especially as technology advances. Companies like SSH Communications Security Oyj are leaders in defensive cybersecurity, focusing on protecting humans, systems, and networks. They're always looking at new ways to strengthen security, which is pretty important given how fast things change.
For example, Suvi Lampila, an SSH fellow, explains that "AI enables attackers to move horizontally within systems in seconds—turning a single crack into complete control almost instantly." This highlights the need for even stronger, more adaptive security measures for IoT devices. SSH, with its robust authentication and encryption, remains a core component in this defense. It's a foundational piece that helps protect against these sophisticated attacks, making sure your remote IoT devices stay safe today and into the future, as a matter of fact. To learn more about how secure shells work, you might want to check out this resource on SSH Academy.
Learn more about secure remote access on our site, and link to this page for advanced IoT device management strategies.
Frequently Asked Questions
Here are some common questions people often have about using SSH with IoT devices:
How do I securely connect to my IoT device?
The most secure way to connect to your IoT device is by using SSH with key-pair authentication. This involves generating a public and private key pair on your computer and then placing the public key on your IoT device. This method is much safer than relying on passwords alone, which can be vulnerable to guessing or brute-force attacks, you know?
What are the benefits of using SSH for IoT?
Using SSH for your IoT devices offers several big benefits. First, it provides strong encryption for all data exchanged, keeping your commands and information private. Second, it offers robust authentication methods, ensuring only authorized users can access your devices. Third, it allows for secure file transfers and remote command execution, making device management from anywhere very practical. It's a pretty comprehensive solution, actually.
Can I transfer files to my remote IoT device with SSH?
Yes, absolutely! SSH includes tools like `scp` (secure copy) and `sftp` (SSH File Transfer Protocol) that allow you to securely copy files and even entire directories between your local machine and your remote IoT device. This is incredibly useful for deploying updates, sending configuration files, or retrieving data logs from your devices, so it's a very common use case.

Remotely ssh to iot device
Remote IoT Behind Router Example Raspberry Pi: A Comprehensive Guide

How To Access And Control Your Devices From Anywhere Using Ssh Remote