Safeguarding Your Information: Understanding The Concept Of An Asianleak In Today's Digital World
In our interconnected world, where information flows freely, the thought of a "leak" can bring about a real sense of worry. It's a feeling many people know, that quiet concern about personal details or important data somehow finding its way into the wrong hands. This idea, which we're calling an "asianleak" for this discussion, points to any instance where private information gets out without permission. It's a broad concept, really, covering anything from a tiny bit of data slipping away to a much larger, more noticeable exposure.
Thinking about this kind of unintended release is important for everyone, whether you're just someone browsing the internet or a business trying to keep its operations secure. The digital spaces we inhabit are, in a way, full of these possibilities. So, understanding how these "leaks" can happen, and what they truly mean for your own digital presence, becomes quite a necessary part of being online today.
This article will take a closer look at what makes information vulnerable, how certain parts of our digital systems, like placeholders for data, play a part, and what practical steps you can take to build a stronger defense for your valuable information. We'll also touch on what the future might hold for keeping our digital lives safe. It's about feeling more in control, you know, of your own digital footprint.
Table of Contents
- Understanding Digital Vulnerabilities
- The Role of Placeholders and Data Polling in Security
- Practical Steps to Guard Your Information
- Building a Stronger Digital Defense
- Looking Ahead: The Future of Information Protection
- Frequently Asked Questions About Data Security
Understanding Digital Vulnerabilities
When we talk about an "asianleak" in this context, we're really talking about any moment when data, something meant to stay private, ends up being seen by people who shouldn't see it. This can happen in so many ways, and it's not always about a big, dramatic event. Sometimes, it's just a tiny bit of information that slips out, almost unnoticed, yet it could still cause problems down the line. It's like finding a single, unexpected answer to a crossword clue, you know, where you thought you had all the pieces perfectly sorted, but then something new pops up.
The reasons behind these exposures are quite varied. It might be something as simple as someone clicking on a bad link in an email, or perhaps a piece of software that has a small flaw, a kind of digital crack, that someone else figures out how to use. Other times, it's about how we manage our own information, like using the same password for many different online accounts. That, basically, makes one weak spot a potential entry point for many places.
Understanding these different forms of vulnerability is the first big step in protecting yourself. It's about recognizing that every piece of information you put online, every account you create, and every interaction you have, carries some level of risk. So, being aware of where your data could be exposed, and how that might happen, helps you to be more careful. It's a bit like learning the rules of a complex game, where knowing the potential pitfalls helps you play better, really.
The Role of Placeholders and Data Polling in Security
It's interesting to think about how some of the basic building blocks of our digital systems can, in a way, relate to the idea of an "asianleak." Take, for instance, the concept of a "placeholder." In computer systems, a placeholder is often just a temporary spot for data, something that holds a place until the real information comes along, or maybe it's just a stand-in for something that will be displayed later. We see this with forms on websites, you know, where there's a blank space waiting for you to type in your name or email. If these placeholders, or the data that eventually fills them, aren't handled with great care, they could, in some respects, become a point where information might accidentally "leak" out.
Then there's "polling," which is another technical idea that has a part to play. Polling, in simple terms, is when a system regularly checks another system for new information or updates. It's like a constant query, always asking, "Is there anything new for me?" This process is very common for keeping apps and websites fresh with the latest data. However, if the way this polling happens isn't secure, if the connection isn't properly locked down, then the data being polled could, arguably, be intercepted or exposed. It's a bit like leaving a door slightly ajar when you're checking for mail, allowing someone else to peek inside.
Think about it like this: just as a crossword solver works to find specific answers from a vast pool of possibilities, our digital systems are constantly processing and retrieving data. The challenge is ensuring that only the intended "answers" or pieces of information are retrieved, and that they only go to the right "solver." When you have placeholder data, or when systems are polling for updates, there's always a need for a very strong underlying structure to prevent any unintended "asianleak." It means making sure the data isn't just sitting there, waiting to be picked up by anyone, but that it's protected at every step, basically, from its source to its destination.
Practical Steps to Guard Your Information
Protecting your information from an "asianleak" is, in some respects, about putting a few simple, yet very effective, habits into practice. One of the most important things you can do is to create very strong passwords. These aren't just any old words; they are long, complex combinations of letters, numbers, and symbols that are incredibly difficult for others to guess. And, as a matter of fact, it's really important to use a different, unique password for every single online account you have. This way, if one account ever gets compromised, the others remain safe, which is a pretty good safeguard.
Another crucial step involves setting up what's called two-factor authentication, or 2FA, wherever it's offered. This means that even if someone manages to get your password, they still need a second piece of information, like a code sent to your phone, to get into your account. It's like having two locks on your door instead of just one, you know, making it twice as hard for anyone to get through. Many services offer this now, and it's a very easy way to add a layer of protection.
Being careful about what you share online is also a big part of keeping your data safe. Think twice before posting personal details, like your full birthdate or your home address, on social media or other public platforms. Once something is out there, it's very hard to pull it back. Similarly, be very wary of suspicious emails or messages that ask for your personal information, like bank details or passwords. These are often "phishing" attempts, and they are designed to trick you into giving away your data. If something feels off, it probably is, and it's always better to be safe than sorry, that's for sure.
Keeping your software updated, including your operating system, web browser, and any apps you use, is another vital practice. Software updates often include security patches that fix known vulnerabilities, which are basically weaknesses that could be exploited by someone looking to cause an "asianleak." When you put off these updates, you're leaving those digital doors open, so to speak, for longer than you should. It's a simple habit, but it makes a significant difference in your overall digital defense, actually.
Building a Stronger Digital Defense
To truly build a stronger defense against any potential "asianleak," it's helpful to think about where your valuable information actually resides. Is it on your computer? Is it stored in the cloud? Is it on your phone? Knowing where your data lives helps you understand what needs protecting. For instance, making regular backups of your important files, like documents and photos, is a very smart move. If something happens to your primary device, you'll still have copies of your precious data, you know, safe and sound elsewhere.
Another area to consider is your privacy settings on social media and other online platforms. Many of these services offer robust options to control who sees your posts, your profile information, and even your location. Taking the time to go through these settings and adjust them to your comfort level can greatly reduce the amount of personal data that is publicly visible. It's about taking charge of your own digital presence, basically, and deciding what you're comfortable sharing with the wider world.
When you download new apps or sign up for new online services, it's also a good idea to pay attention to the permissions they ask for. Does a simple game really need access to your contacts or your microphone? Probably not. Being a bit discerning about what you allow apps to do can prevent them from gathering more information than they truly need. This kind of careful choice, in a way, helps to close off potential avenues for an "asianleak" before they even open up.
It's also about fostering a general sense of awareness when you're online. If something seems too good to be true, it probably is. If a website looks a bit suspicious, it might be. Trusting your instincts and taking a moment to verify things before you click, download, or share can save you a lot of trouble. This ongoing vigilance is a key part of maintaining your digital safety, obviously, and it helps you avoid many common traps that lead to information exposure.
Looking Ahead: The Future of Information Protection
The landscape of information protection is always changing, and it's something that truly keeps evolving. As technology moves forward, so too do the ways in which data can be exposed, and, consequently, the methods we use to keep it safe. The idea of an "asianleak" will, in some respects, always be a concern, but the tools and strategies to combat it are constantly getting better. New technologies, like advanced encryption methods and artificial intelligence that can spot unusual activity, are being developed to help us guard our information more effectively. It's a bit like the ongoing effort to improve a crossword solver, always finding more efficient and accurate ways to get to the right answer, you know, and protect against wrong ones.
For individuals, staying informed about the latest security practices and emerging threats will always be important. It's not a one-time fix; it's an ongoing commitment to learning and adapting. What works today might need an update tomorrow. Regularly reviewing your online habits and updating your security settings will help ensure your defenses are as strong as they can be against any potential "asianleak."
Furthermore, the collective effort of many people and organizations plays a big part in creating a safer digital environment for everyone. When companies prioritize security in their products and services, and when governments put in place policies that protect privacy, it benefits us all. So, supporting those efforts and choosing services that demonstrate a strong commitment to data protection helps to build a more secure future for everyone's information. At the end of the day, it's a shared responsibility, really, to keep our digital world a safer place for all.
Frequently Asked Questions About Data Security
What is the biggest risk to my online data?
Honestly, one of the biggest risks to your online data often comes from human error, like falling for phishing scams or using weak, easily guessed passwords. It's also about not keeping your software updated. While sophisticated attacks happen, many exposures start with simpler mistakes, you know, that could be avoided.
How can I tell if my information has been compromised?
You might notice unusual activity on your accounts, like emails you didn't send or login attempts from unfamiliar locations. Sometimes, you'll receive a notification from a service provider if they've experienced a breach. Regularly checking your account activity and using services that monitor for data breaches can also help you find out, basically.
Are there simple ways to improve my digital privacy right now?
Absolutely. You can start by using unique, strong passwords for all your accounts and enabling two-factor authentication wherever possible. Also, take a few moments to review the privacy settings on your social media profiles and other online services. Being mindful of what you click on and what information you share online also makes a huge difference, that's for sure. Learn more about digital safety practices on our site, and you might want to link to this page for more detailed advice.
So, understanding the concept of an "asianleak" in terms of data vulnerability is truly important in our very connected world. Taking steps to protect your information, from using strong passwords to being careful about what you share, really helps. It's an ongoing effort, yes, but one that gives you more peace of mind. Start today, you know, by checking your security settings and making those small but significant changes for your digital safety.

Singapore girl leaked - Page 203 - The Asian Commercial Sex Scene
Asian Scandal Net (1) — Postimages
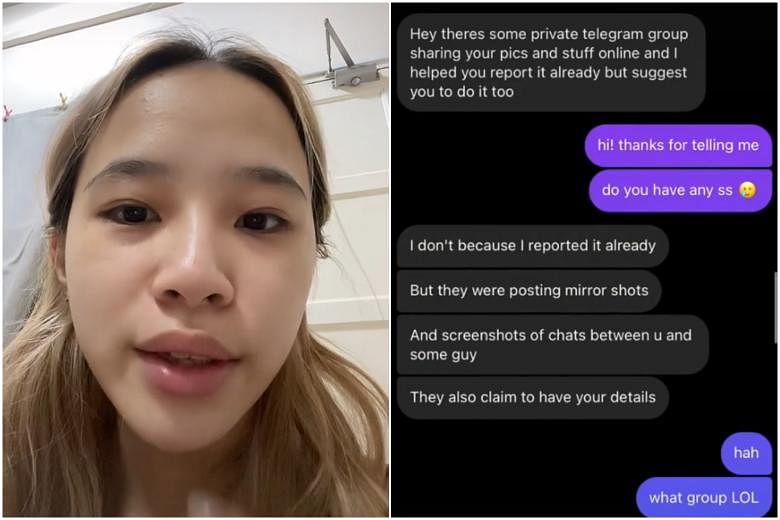
Young women in Singapore targeted in 'leaked photo' scams | The Straits